Statistical bulletin of communication industry in 2020
In 2020, in the face of the severe impact of the COVID-19 epidemic, China’s communications industry resolutely implemented the decision-making arrangements of the CPC Central Committee and the State Council, fully supported the epidemic prevention and control work, actively promoted the construction of a network power, realized the 5G network coverage of all prefecture-level cities in the country, and continuously improved the capacity of new information infrastructure, providing strong support for accelerating the development of the digital economy and building a new development pattern.
First, the industry maintained a stable operation
(A) the growth rate of telecom business income rebounded, and the total telecom business increased rapidly.
According to preliminary accounting, in 2020, the telecom business revenue totaled 1.36 trillion yuan, an increase of 3.6% over the previous year, and the growth rate increased by 2.9 percentage points. According to the price of last year, the total telecommunications business was 1.5 trillion yuan, up 20.6% year-on-year.
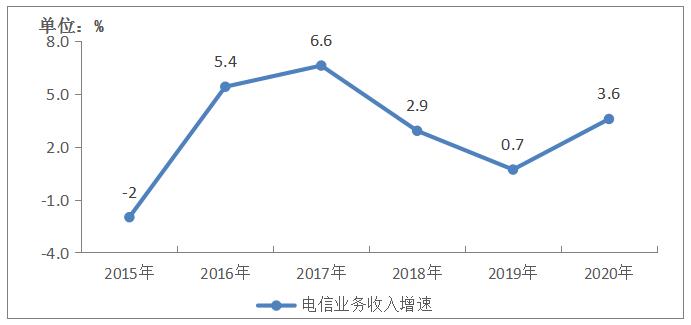
Figure 1-1 Telecom Business Revenue Growth from 2015 to 2020
(B) The fixed communications business grew rapidly, and the driving role of emerging services was obvious.
In 2020, the revenue of fixed communication business reached 467.3 billion yuan, up by 12% over the previous year, accounting for 34.5% of the telecom business revenue, up by 2.8 percentage points over the previous year, and the proportion increased for three consecutive years.
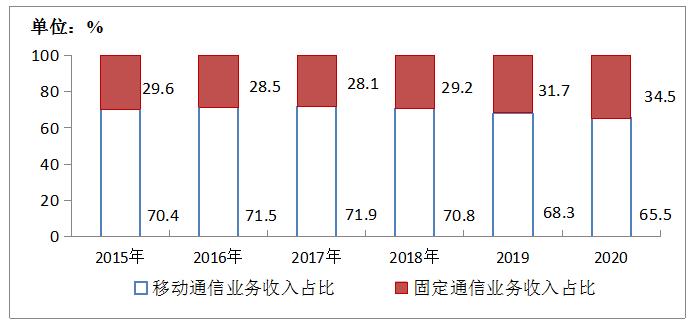
Figure 1-2 Revenue Proportion of Mobile Communication Business and Fixed Communication Business from 2015 to 2020
Apply new technologies such as cloud computing, big data, Internet of Things, artificial intelligence, and vigorously expand emerging businesses, making fixed value-added and other businesses the first engine of growth. In 2020, the revenue of fixed data and Internet services reached 237.6 billion yuan, up by 9.2% over the previous year, and its proportion in the telecom business revenue increased from 16.6% in the previous year to 17.5%, which boosted the telecom business revenue growth by 1.53 percentage points and contributed 42.9% to the telecom business revenue growth of the whole industry. The revenue of fixed value-added services reached 174.3 billion yuan, up by 26.9% over the previous year, and its proportion in telecom business revenue increased from 10.5% in the previous year to 12.9%, which boosted the telecom business revenue growth by 2.82 percentage points and contributed 79.1% to the revenue growth. Among them, the revenue of data center business, cloud computing, big data and Internet of Things business increased by 22.2%, 85.8%, 35.2% and 17.7% respectively over the previous year; IPTV (Internet TV) business revenue was 33.5 billion yuan, up by 13.6% over the previous year.
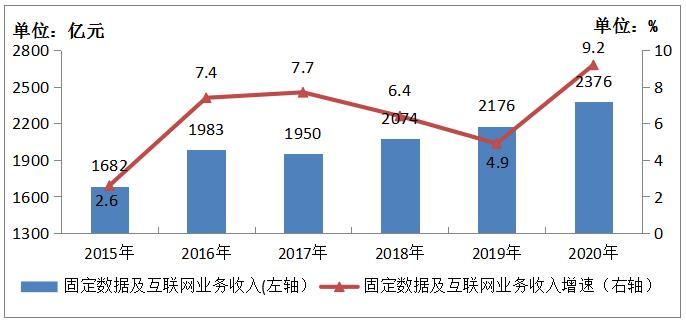
Figure 1-3 Revenue Development of Fixed Data and Internet Services from 2015 to 2020
(3) The proportion of mobile communication services has declined, and data and Internet services are still important sources of income.
In 2020, the revenue of mobile communication business was 889.1 billion yuan, down by 0.4% from the previous year, and its proportion in telecom business revenue dropped to 65.5%, down by 6.4 percentage points from the peak in 2017. Among them, the revenue from mobile data and Internet services was 620.4 billion yuan, up by 1.7% over the previous year, and its proportion in the telecom business revenue dropped from 46.6% in the previous year to 45.7%, which boosted the telecom business revenue growth by 0.79 percentage points and contributed 22.3% to the revenue growth.
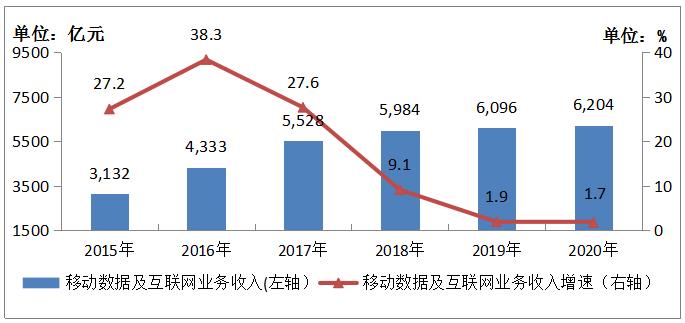
Figure 1-4 Revenue Development of Mobile Data and Internet Services from 2015 to 2020
Second, the network speeds up and the universal service develops in depth.
(1) The scale of mobile phone users declined slightly, and the penetration rate of 4G users exceeded 80%.
In 2020, there will be a net decrease of 16.4 million telephone users nationwide, and the total number will fall back to 1.776 billion. Among them, the total number of mobile phone users was 1.594 billion, with a net decrease of 7.28 million, and the penetration rate was 113.9/100 people, down 0.5/100 people from the end of last year. The total number of 4G users reached 1.289 billion, with a net increase of 6.79 million, accounting for 80.8% of the number of mobile phone users. The total number of fixed telephone users was 182 million, with a net decrease of 9.13 million, and the penetration rate dropped to 13 per 100 people.
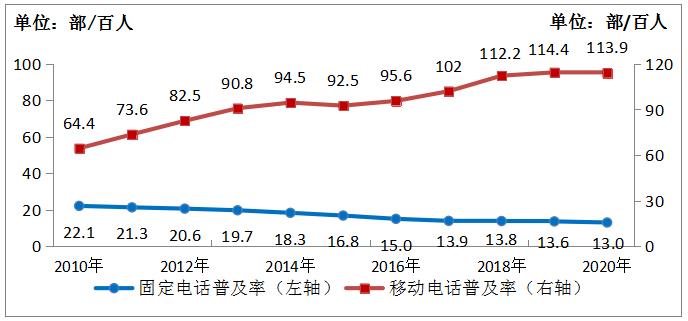
Figure 2-1 Development of fixed-line and mobile phone penetration rate from 2010 to 2020
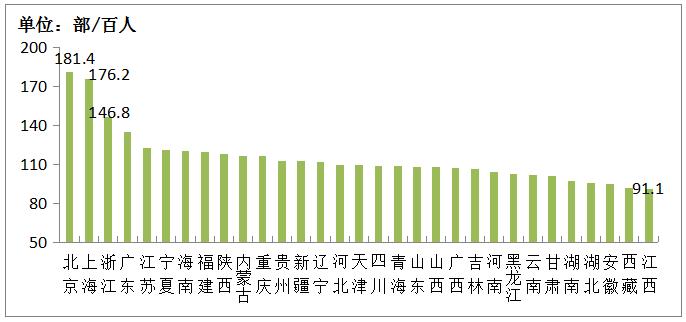
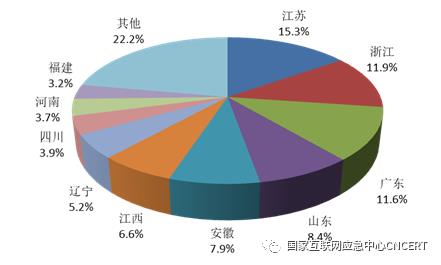
Figure 2-2 Mobile phone penetration rate by province in 2020
(2) Nearly 90% of the 100-megabit broadband is available, and the upgrade to gigabit broadband access is accelerated.
The pace of network speed-up has been accelerated, and the promotion of gigabit broadband services has been continuously promoted. By the end of 2020, the total number of fixed Internet broadband access users of the three basic telecommunications enterprises reached 484 million, with a net increase of 34.27 million. Among them, the total number of fixed Internet broadband access users with access rate of 100Mbps or above reached 435 million, with a net increase of 50.74 million, accounting for 89.9% of the total fixed broadband users, accounting for 4.5 percentage points higher than that at the end of last year; The number of users with access rates of 1000Mbps and above reached 6.4 million, a net increase of 5.53 million over the end of last year.
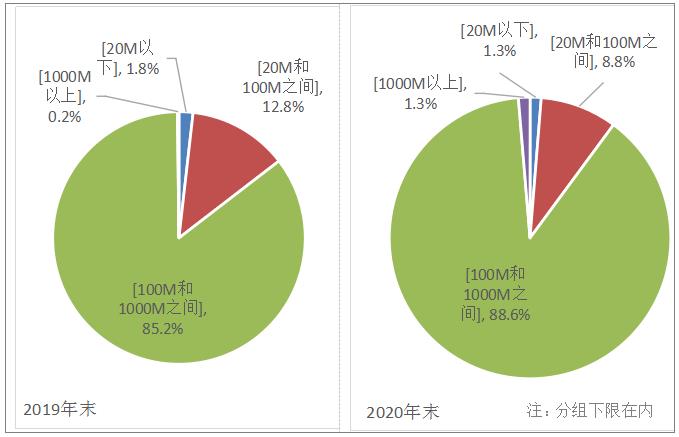
Figure 2-3 Proportion of Fixed Internet Broadband Users with Different Access Rates in 2019 and 2020
(3) Universal telecommunications services continued to advance, and rural broadband users grew rapidly.
By the end of 2020, the total number of rural broadband users in China reached 142 million, with a net increase of 7.12 million, up 5.3% from the end of last year. The proportion of optical fiber and 4G in administrative villages in China exceeds 98%, and the average download rate in the pilot areas of universal telecommunications service exceeds 70M, so that rural areas and cities can achieve "the same network and the same speed".
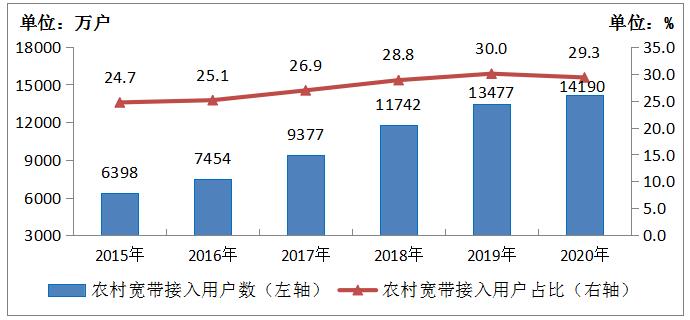
Figure 2-4 Rural Broadband Access Users and Their Proportion in 2015-2020
(D) The development of new formats was accelerated, and the number of cellular Internet of Things users increased rapidly.
Promote transformation and upgrading, accelerate the construction of new infrastructure such as 5G network, Internet of Things, big data and industrial Internet, and promote the deep integration of the new generation of information technology and manufacturing industry, with further results. By the end of 2020, the three basic telecommunications companies had developed 1.136 billion cellular Internet of Things users, with a net increase of 108 million users in the whole year, among which the end users used in intelligent manufacturing, intelligent transportation and intelligent public utilities accounted for 18.5%, 18.3% and 22.1% respectively. The total number of IPTV users reached 315 million, with a net increase of 21.2 million.
Third, the scale of mobile data traffic consumption continues to expand.
(A) Mobile Internet traffic grew rapidly, with the monthly average household traffic (DOU) reaching 10GB.
Affected by the COVID-19 epidemic and the new lifestyle of "staying at home", the demand for mobile Internet applications has surged, and online consumption has been extremely active. Short video, live broadcast and other high-traffic application scenarios have driven the rapid growth of mobile Internet traffic. In 2020, the consumption of mobile Internet access traffic reached 165.6 billion GB, an increase of 35.7% over the previous year. The average monthly mobile Internet traffic (DOU) reached 10.35GB/ household month, an increase of 32% over the previous year. In December, the DOU was as high as 11.92GB/ household month. Among them, mobile Internet traffic reached 156.8 billion GB, up 29.6% over the previous year, accounting for 94.7% of the total traffic.
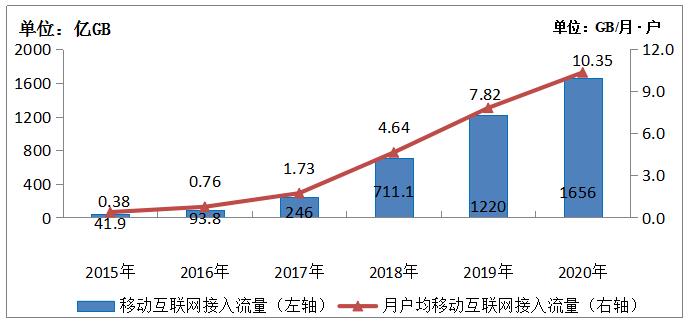
Figure 3-1 Mobile Internet Traffic and Monthly DOU Growth from 2015 to 2020
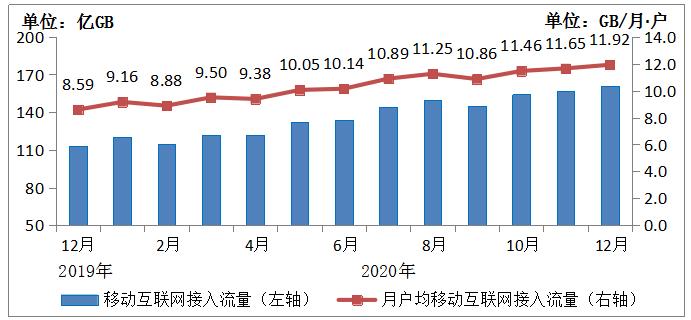
Figure 3-2 Current Traffic and DOU of Mobile Internet Access in 2020
(B) Mobile SMS business is still out of sync, voice business continues to decline.
In 2020, the national mobile SMS business volume increased by 18.1% over the previous year, and the growth rate decreased by 14.1 percentage points over the previous year; The revenue of mobile short message service increased by 2.4% compared with the previous year, and the growth difference of mobile short message service decreased from 33% in the previous year to 15.7%. The influence of Internet application on voice service substitution continues to deepen. In 2020, the length of outgoing calls on mobile phones nationwide was 2.24 trillion minutes, down 6.2% from the previous year.
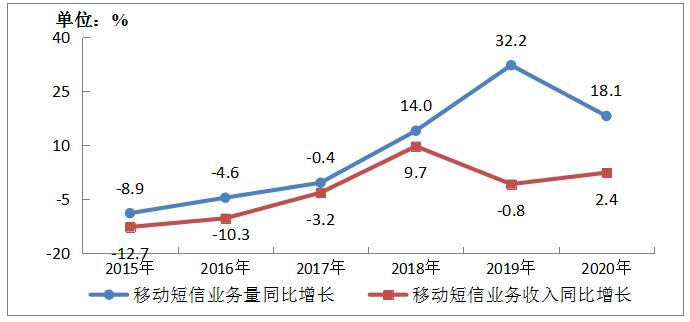
Figure 3-3 Growth of Mobile SMS Business and Revenue from 2015 to 2020
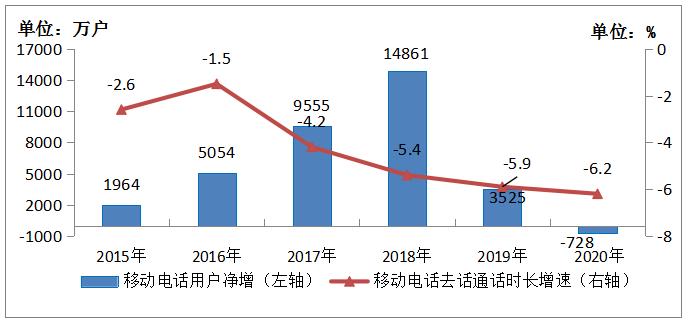
Figure 3-4 Growth of Mobile Phone Users and Calls from 2014 to 2019
Fourth, the network infrastructure capacity continued to upgrade.
(1) Investment in fixed assets grew rapidly, and the proportion of mobile investment continued to rise.
In 2020, the three basic telecommunications companies and China Tower Co., Ltd. completed a total investment of 407.2 billion yuan in fixed assets, an increase of 11% over the previous year, and the growth rate increased by 6.3 percentage points. Among them, the investment in fixed assets of mobile communication ranked first, with an investment of 215.4 billion yuan, accounting for 52.9% of the total investment, accounting for 5.1 percentage points higher than that of the previous year.
(2) The network infrastructure was optimized and upgraded, and the construction of 5G networks was steadily advanced.
Accelerate the construction of 5G networks, constantly eliminate blind spots in network coverage, improve network quality, enhance network supply and service capabilities, and continuously make new progress in the construction of a new generation of information and communication networks. In 2020, the length of new optical cable lines will be 4.28 million kilometers, and the total length of national optical cable lines has reached 51.69 million kilometers. By the end of 2020, the number of Internet broadband access ports reached 946 million, a net increase of 30.27 million over the end of last year. Among them, FTTH/0 ports reached 880 million, a net increase of 43.61 million over the end of last year, and the proportion of Internet access ports increased from 91.3% at the end of last year to 93%. The number of xDSL ports dropped to 6.49 million, accounting for 0.7%.
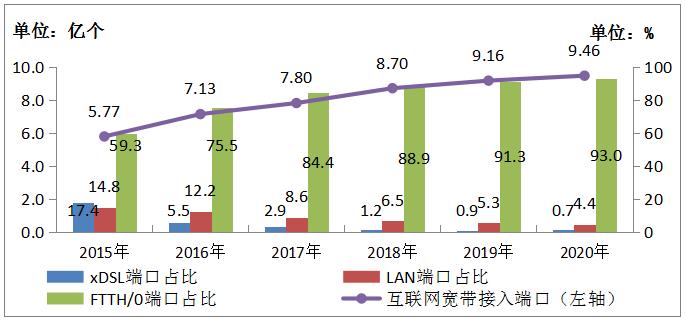
Figure 4-1 Development of Internet Broadband Access Ports from 2015 to 2020
In 2020, the total number of mobile communication base stations in China will reach 9.31 million, with a net increase of 900,000. Among them, the total number of 4G base stations reached 5.75 million, and urban areas achieved deep coverage. The construction of 5G network has been steadily advanced. According to the principle of moderate advancement, more than 600,000 new 5G base stations have been built, and all of them have opened more than 718,000. Among them, China Telecom and China Unicom have jointly built and shared more than 330,000 5G base stations, and the 5G network has covered cities above prefecture level and key counties and cities in China.
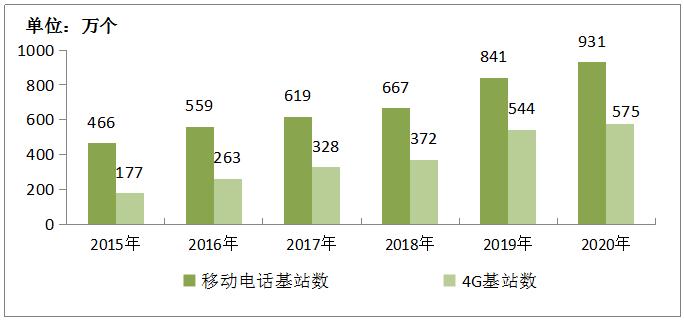
Figure 4-2 Development of Mobile Phone Base Station from 2015 to 2020
V. Coordinated development of the eastern, central and western regions
(A) the share of telecom business revenue by region is relatively stable.
In 2020, the proportion of telecom business revenue in the eastern and western regions will be 51% and 23.7% respectively, both increasing by 0.1 percentage points over the previous year; The central proportion was 19.6%, which was the same as the previous year; Northeast China accounted for 5.6%, down 0.2 percentage points from the previous year.
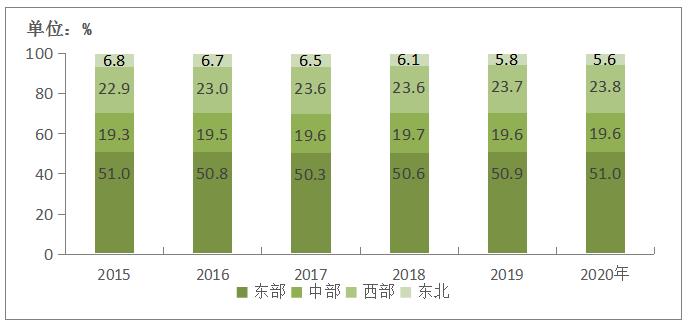
Figure 5-1 Proportion of Telecom Business Revenue in East, Central, West and Northeast China from 2015 to 2020
(2) The proportion of users with 100 megabits and above fixed Internet broadband access in Northeast China is leading.
By the end of 2020, the number of fixed Internet broadband access users with 100Mbps or above in the eastern, central, western and northeastern regions reached 186.18 million, 108.38 million, 113.86 million and 26.2 million respectively, accounting for 88.9%, 90.8%, 90.3% and 91.2% of the broadband access users in this region, accounting for 2.8% and 91.2% higher than the previous year respectively.

Figure 5-2 penetration rate of fixed broadband access users with 100Mbps or above in the eastern, central, western and northeastern regions from 2016 to 2019.
(3) The growth rate of mobile Internet traffic in the western region leads the country.
In 2020, the mobile Internet access traffic in the eastern, central, western and northeastern regions will reach 70 billion GB, 35.7 billion GB, 50.5 billion GB and 9.34 billion GB respectively, up by 31.9%, 36.5%, 42.3% and 29% respectively over the previous year. The growth rate in the western region is 10.4, 5.8 and 13.3 higher than that in the eastern, central and northeastern regions respectively. In the month of December, the average household flow in the west reached 13.81/ household month, which was 2.02GB, 3.25GB and 3.78GB higher than that in the east, middle and northeast respectively.
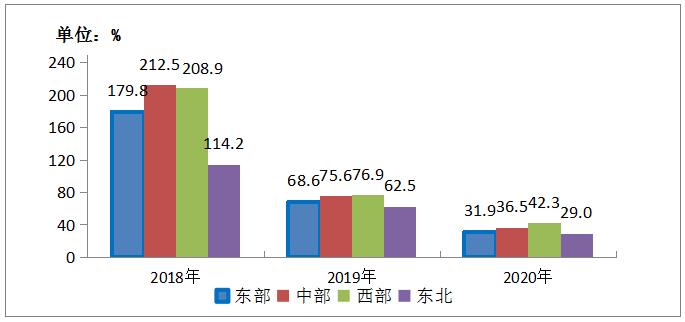
Figure 5-3 Growth of Mobile Internet Access Traffic in East, Central, West and Northeast China from 2015 to 2020