In order to fully reflect the spread of malicious programs, vulnerability risks, DDoS attacks, website security and other aspects of China’s Internet in the first half of 2020, CNCERT combed the monitoring data in the first half of the year and formed the monitoring data analysis report as follows. To download the report, please click the attachment at the end of the article.
catalogue
First, malicious programs
(A) computer malicious program capture
(2) Infection of users of computer malicious programs
(3) Malicious mobile Internet programs
(4) Malicious programs for networked smart devices
Second, security vulnerabilities
Third, denial of service attacks
(A) the active situation of attack resources
(2) The situation of large-volume attacks in China
(3) The activity of mainstream attack platforms
Fourth, website security
(A) phishing
(2) The back door of the website
(C) Web tampering
V. Cloud platform security
Six, industrial control system safety
(A) exposure of industrial control system on the Internet side
(II) Threat monitoring on the Internet side of industrial control system
(3) Information on safety loopholes of industrial control products
First, malicious programs
(A) computer malicious program capture
In the first half of 2020, about 18.15 million samples of computer malicious programs were captured, with an average daily spread of more than 4.83 million times, involving about 11,000 families of computer malicious programs. According to the statistics of communication sources, overseas malicious programs mainly come from the United States, Seychelles and Canada, and the specific distribution abroad is shown in Figure 1. Malicious programs located in China mainly come from Zhejiang, Guangdong and Beijing. According to the target IP statistics, there are about 42.08 million IP addresses attacked by computer malicious programs in China, accounting for 12.4% of the total IP addresses in China. These attacked IP addresses are mainly concentrated in Shandong Province, Jiangsu Province, Guangdong Province, Zhejiang Province, etc. The distribution of IP addresses attacked by computer malicious programs in China is shown in Figure 2.
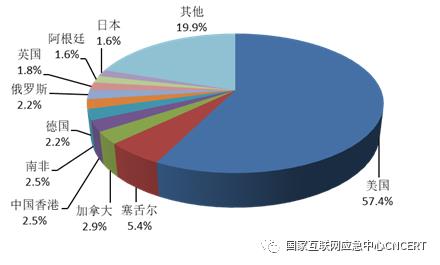
Figure 1 Distribution of computer malicious code propagation sources outside China
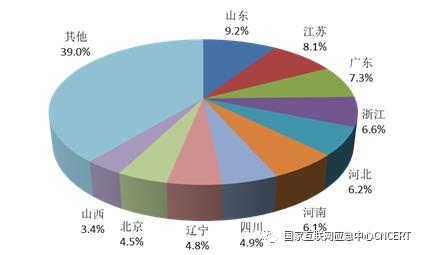
Fig. 2 IP distribution under computer malicious code attack in China
(2) Infection of users of computer malicious programs
The number of hosts infected with computer malicious programs in China is about 3.04 million, up 25.7% year-on-year. About 25,000 computer malicious program control servers located abroad control about 3.03 million hosts in China. In terms of the countries or regions where the control servers belong, the number of control servers located in the United States, China, Hong Kong and the Netherlands ranks in the top three, with about 8,216, 1,478 and 1,064 respectively, with specific distribution as shown in Figure 3; In terms of the number of hosts controlled in China, the control scales of control servers located in the United States, the Netherlands and Germany rank the top three, controlling about 2.52 million, 1.27 million and 1.17 million hosts in China respectively, as shown in Figure 4. In addition, according to the sampling monitoring data, it is found that attacks against IPv6 networks have also begun to appear, and computer malicious program control servers with about 1,200 IPv6 addresses abroad have controlled about 15,000 IPv6 address hosts in China.
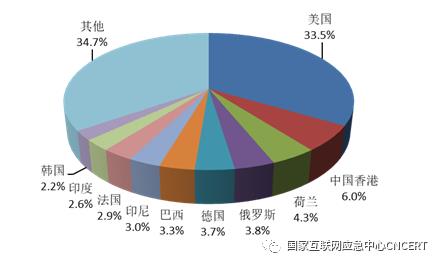
Fig. 3 Distribution of control terminals of overseas Trojan botnets that control hosts in China.
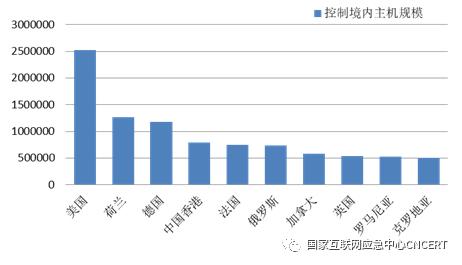
Figure 4 Countries or regions that control the number of TOP10 hosts in China.
From the regional distribution of the number of hosts infected with computer malicious programs in China, they are mainly distributed in Jiangsu Province (accounting for 15.3% of the infected number in China), Zhejiang Province (accounting for 11.9%), Guangdong Province (accounting for 11.6%), etc. The specific distribution is shown in Figure 5. Among botnets infected with malicious computer programs, there are 4,696 botnets with a scale of more than 100 hosts and 16 botnets with a scale of more than 100,000, as shown in Figure 6. Relevant institutions have disposed of 45 botnets with large control scale, effectively controlling the harm caused by computer malicious programs infecting the host.
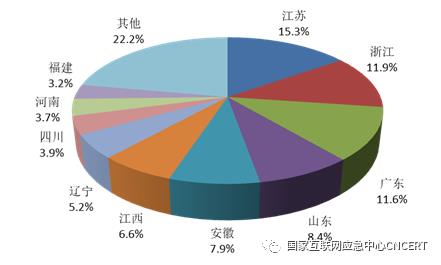
Figure 5 The number of hosts infected with Trojan bots in China is distributed by region.
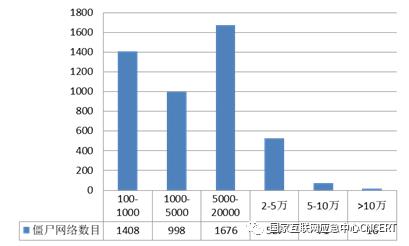
Figure 6 Scale distribution of botnets
(3) Malicious mobile Internet programs
Through independent capture and vendor exchange, more than 1.63 million malicious mobile Internet programs were discovered, up 58.3% year-on-year. Through the statistics of malicious behavior of malicious programs, it is found that the top three are still hooliganism, tariff consumption and information theft, accounting for 36.5%, 29.2% and 15.1% respectively. In order to effectively prevent the harm of malicious programs on the mobile Internet and strictly control the spread of malicious programs on the mobile Internet, 812 malicious programs on 125 platforms providing mobile application download services in China have been removed, effectively preventing the harm of malicious programs on the mobile Internet and strictly controlling the spread of malicious programs on the mobile Internet.
In recent years, China has gradually increased the security management of App stores and Applications, requiring App stores to conduct real-name audits of developers who put apps on the shelves, and conduct security inspections and content copyright audits on apps, which makes it more difficult for Internet black-market app stores to spread malicious apps. At the same time, however, the "edge-ball" gray applications that can evade supervision and achieve bad purposes have increased. For example, counterfeit apps with fishing purposes and fraudulent behaviors have become an important tool for illegal production, which continues to pose a greater threat to users in important industries such as finance, transportation and telecommunications. In the first half of 2020, 180 new download links of counterfeit apps were discovered through independent monitoring and complaint reporting. These counterfeit apps have the characteristics of easy copying, frequent version updates, and rapid spread of hot spots. They are mainly concentrated in popular applications such as counterfeit public security law, banking, social software, payment software, and ticketing software. The counterfeiting methods are mainly counterfeit names, icons, pages, etc., which are very deceptive. At present, because developers need to submit proof materials such as software copyright before Applying for the Application in the app store, it is difficult for counterfeit apps to be put on the app store, and its circulation channels are mainly concentrated in other online communication channels such as network disk, cloud disk and advertising platform.
(4) Malicious programs for networked smart devices
At present, there are more than 15 malicious programs active on smart devices, including Mirai, Gafgyt, Dofloo, Tsunami, Hajime, MrBlack, Mozi, PinkPot and so on. These malicious programs generally invade and control smart devices through vulnerabilities and violent cracking. After being controlled by intrusion, there are security threats and risks such as user information and device data being stolen, hardware devices being controlled and destroyed, devices being used as a springboard to attack other hosts in the intranet or launching DDoS attacks abroad. In the first half of the year, about 1.26 million malicious programs were found on smart devices, most of which belonged to Mirai family and Gafgyt family, accounting for more than 96.0%. There are more than 50,000 IP addresses in the server, and the number of IP addresses of suspected infected smart devices in China is about 920,000, which is basically the same as that in the first half of 2019, mainly located in Zhejiang, Jiangsu, Anhui, Shandong and Liaoning provinces. The accused networked smart devices launched DDoS attacks on more than 1,000 targets every day, which was basically the same as that in the first half of 2019.
Second, security vulnerabilities
The National Information Security Vulnerability Sharing Platform (CNVD) included 11,073 general security vulnerabilities, a substantial increase of 89.0% year-on-year. Among them, the number of high-risk vulnerabilities was 4,280 (accounting for 38.7%), up 108.3% year-on-year, and the number of "zero-day" vulnerabilities was 4,582 (accounting for 41.4%), up 80.7% year-on-year. Security vulnerabilities mainly cover vendors or platforms such as Google, WordPress and Oracle Bone Inscriptions. According to the statistics of the affected objects, the top three are application vulnerabilities (48.5%), Web application vulnerabilities (26.5%) and operating system vulnerabilities (10.0%), as shown in Figure 7. In the first half of 2020, CNVD handled nearly 15,000 incidents involving network security vulnerabilities such as government agencies and important information systems.
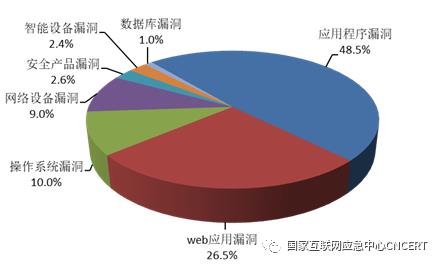
Figure 7CNVD includes statistics of security vulnerabilities classified by affected objects.
Third, denial of service attacks
Due to the characteristics of low attack cost and obvious attack effect, DDoS attack is still one of the most common and influential network security threats faced by Internet users. Sampling monitoring found that the number of high-traffic DDoS attacks with daily peak traffic exceeding 10Gbps in China was basically the same as that in 2019, with about 220 incidents.
(A) the active situation of attack resources
After continuous monitoring, analysis and disposal, the stability of available DDoS attack resources is reduced, and the number of available active resources is controlled at a low level. Cumulative monitoring found 2,379 active C&C control servers for launching DDoS attacks, of which 95.5% were located abroad, mainly from the United States, the Netherlands, Germany, etc. There are about 1.22 million active controlled hosts, of which 90.3% are from China, mainly from Jiangsu, Guangdong, Zhejiang, Shandong and Anhui provinces. There are about 8.01 million reflection attack servers, of which 67.4% are from China, mainly from Liaoning, Zhejiang, Guangdong, Jilin and Heilongjiang provinces.
(2) The situation of large-volume attacks in China
During the monitoring, it is found that the main attack methods are still TCP SYN Flood, NTP Amplification, SSDP Amplification, DNS Amplification and UDP Flood.The above five attacks accounted for 82.9%. In order to avoid traceability, attackers tend to use these attack methods which are easy to hide the attack source, and flexibly combine the attack traffic according to the protection of the attack target, and the proportion of mixed attack methods is 16.4%. In addition, with the rampant "DDoS as a service" black production mode in recent years, attackers tend to use high-traffic attacks to instantly paralyze the target network. The proportion of attacks with DDoS attack duration less than half an hour is 81.5%, and the targets are mainly located in Zhejiang, Jiangsu, Fujian, Shandong, Guangdong and Beijing, accounting for 81.1%.
(3) The activity of mainstream attack platforms
Through continuous monitoring and tracking of the activity of DDoS attack platforms, it is found that DDoS attack platforms on web pages and botnet families such as Gafgyt, Mirai, Xor, BillGates and Mayday are still active, and there are many DDoS attacks. As one of the black production modes of "DDoS as a service", the web page DDoS attack platform provides services directly to users, and users can launch attacks on their own as needed, which greatly reduces the difficulty of launching DDoS attacks and leads to further proliferation of DDoS attacks. The monitoring found that the number of DDoS attacks initiated by the web DDoS attack platform was the largest, increasing by 32.2% compared with the first half of 2019. At present, a large number of active Internet of Things devices lacking security protection on the Internet provide a large number of controlled resources for the rampant development of DDoS attack platforms, resulting in a high number of DDoS attacks. New variants of Gafgyt and Mirai malicious programs appear constantly, which keeps the number of botnet control terminals and attack events formed by them at a high level, while Xor malicious program family has obvious characteristics that it provides "DDoS as a service" black-market business, showing that it maintains a high attack frequency with a small number of control terminals.
Fourth, website security
(A) phishing
The monitoring found that there were about 19,000 counterfeit pages for websites in China. CNCERT mainly disposed of 6,226 counterfeit pages such as online business halls in the financial industry and telecommunications industry, with a year-on-year decrease of 48.1%. In the coordinated disposal of counterfeit pages, the IP address of the counterfeit page still ranks first in China and Hongkong, accounting for 74.0%. At the same time, the number of counterfeit pages on the "ETC online authentication" website on the internet has increased by spurt. After entering May, the number of phishing pages related to "ETC online authentication" accounted for as high as 61.2%, and the main IP addresses of such phishing websites are still located abroad. The forms of counterfeiting mainly include different page themes such as "ETC information authentication", "ETC online authentication" and "ETC online authentication center", and fraudsters trick users into submitting personal privacy information such as real name, bank card account number, ID number, bank reserved mobile phone number and withdrawal password.
(2) The back door of the website
About 18,000 IP addresses at home and abroad have implanted backdoors into about 35,900 websites in China, and the number of websites implanted with backdoors in China has increased by 36.9% compared with the first half of 2019. Among them, there are about 18,000 overseas IP addresses (accounting for 99.3% of all IP addresses) that have implanted backdoors into about 35,700 websites in China, with the most IP addresses located in the United States, accounting for 19.0% of the total overseas IP addresses, followed by IP addresses located in the Philippines and China, as shown in Figure 8. In terms of controlling the total number of websites in China, IP addresses located in the Philippines control the largest number of websites in China, about 13,600, followed by IP addresses located in China, Hongkong and the United States, which control 7,300 and 6,020 websites in China respectively. In addition, with the accelerated deployment of IPv6 in China, the scope of websites supporting IPv6 is expanding. In addition, there were 592 backdoor incidents of websites whose attack source and target were IPv6 addresses, involving a total of 35 attack source IPv6 addresses and 72 domain names of attacked IPv6 address resolution websites.
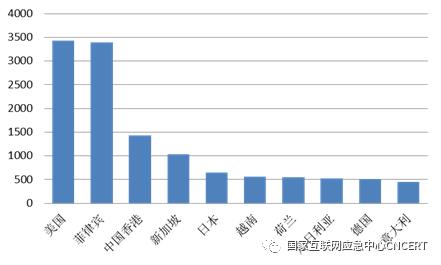
Figure 8 TOP10 of the country or region where the backdoor IP address is implanted into the website in China from overseas.
(C) Web tampering
There are about 74,000 websites that have been tampered with in China, including 318 government websites that have been tampered with. Judging from the distribution of top-level domain names of tampered web pages in China, ".com", ".net" and ".org" still rank in the top three, accounting for 74.1%, 5.1% and 1.7% of the total respectively, as shown in Figure 9.
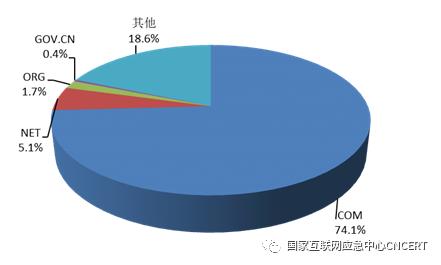
Figure 9 Distribution of tampered websites in China by top-level domain name
V. Cloud platform security
The situation of network security threats on China’s cloud platforms is still grim. First of all, the proportion of all kinds of network security incidents that occurred on the mainstream cloud platforms in China is still high. Among them, the number of DDoS attacks on the cloud platform accounts for 76.1% of the attacks on domestic targets, the number of embedded backdoor links accounts for 90.3% of all embedded backdoor links in China, and the number of tampered pages accounts for 93.2% of the number of tampered pages in China. Secondly, attackers often use China’s cloud platform to launch cyber attacks. Among them, the number of DDoS attacks initiated by the cloud platform as the control terminal accounts for 79.0% of the number of DDoS attacks initiated by domestic control, the number of IP addresses of controlled terminals controlled by malicious programs such as Trojans and botnets accounts for 96.3% of all IP addresses of controlled terminals in China, and the number of malicious programs carried by them accounts for 79.0% of the number of malicious programs carried on the domestic Internet.
Six, industrial control system safety
(A) exposure of industrial control system on the Internet side
Monitoring found that 4,630 industrial devices were exposed to the Internet, involving 47 types of devices, such as programmable logic controllers, intelligent buildings and data acquisition, from 35 domestic and foreign manufacturers. The specific types are shown in Figure 10. Among them, the equipment with high-risk vulnerabilities accounts for about 41%. The monitoring found 480 sets of networked monitoring and management systems exposed in key industries such as electric power, oil and gas, urban rail transit, etc., including 262 sets of electric power, 118 sets of oil and gas, and 100 sets of urban rail transit. The types involved include government supervision platform, remote monitoring, asset management, engineering safety, data detection system, pipe network dispatching system, OA system, cloud platform, etc. The specific platform types are shown in Figure 11. Among them, about 11.1% systems have high-risk vulnerabilities such as information leakage, cross-site request forgery and improper input verification. Once the industrial control system exposed to the Internet is attacked, it will seriously threaten the safety of the production system.
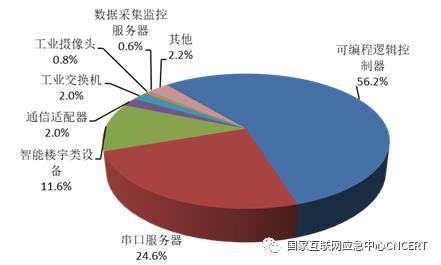
Fig. 10 Type statistics of networked industrial equipment discovered by monitoring.
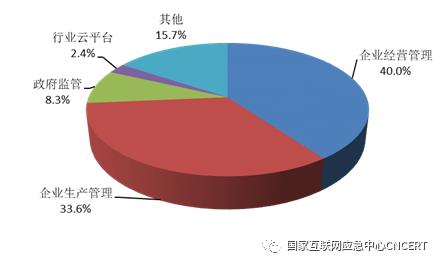
Figure 11 Statistics on the types of networked monitoring management systems in key industries discovered by monitoring.
(II) Threat monitoring on the Internet side of industrial control system
The network assets of domestic industrial control systems continue to be scanned and sniffed from abroad, with an average of more than 20,000 times a day. Through analysis, the sniffing behavior originated from 90 countries such as the United States, Britain and Germany, and the target involved networked industrial control equipment and systems in key industries such as energy, manufacturing and communication. A large number of network assets information of key information infrastructure and its networked control system are sniffed abroad, which brings hidden dangers to cyberspace security in China. China’s large industrial cloud platforms, such as Genyun, Aerospace Cloud, OneNET, COSMOPlat, Aopu Cloud and Jizhiyun, continue to suffer from network attacks from abroad, with an average number of attacks of 114 times per day, up 27% year-on-year. The types of attacks are shown in Figure 12, involving remote code execution, denial of service, Web vulnerability exploitation, etc. Industrial cloud platforms carry a large number of access devices, business systems, as well as enterprise, personal information and important data.
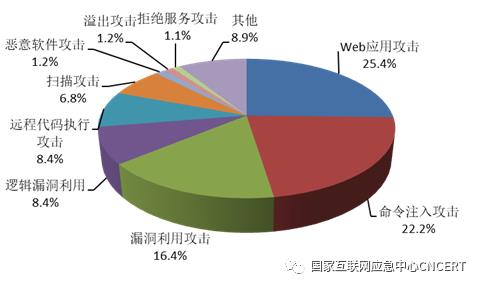
Figure 12 Type distribution of attack events of industrial cloud platform
(3) Information on safety loopholes of industrial control products
The four vulnerability platforms of CNVD, CVE, NVD and CNNVD newly included 323 vulnerabilities of industrial control system products, of which high, medium and dangerous vulnerabilities accounted for 94.7%. As shown in Figure 13 and Figure 14, the products affected by the vulnerability are widely used in key information infrastructure industries such as manufacturing, energy, water treatment, information technology, chemical industry, transportation, commercial facilities, agriculture, water conservancy projects, government agencies, etc. The product suppliers involved in the vulnerability mainly include ABB, Wanke, Siemens, Advantech, Schneider, Mossa, Mitsubishi, Haiwei, Asia Control and Yonghong.
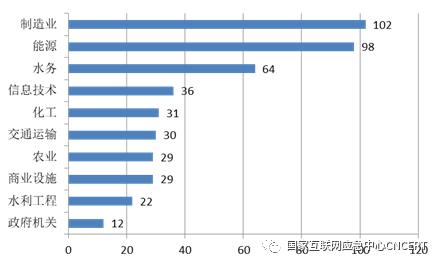
Figure 13 Industrial distribution of new industrial control product vulnerabilities TOP10 (Note: products affected by vulnerabilities can be applied to multiple industries)
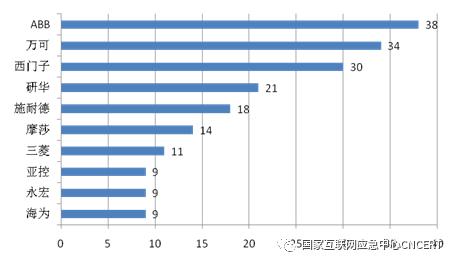
Figure 14 Supplier Distribution of Newly Added Industrial Control Product Vulnerabilities TOP1
Attachment: Analysis Report on China’s Internet Network Security Monitoring Data in the First Half of 2020