At 8 o’clock, witness the news every day. CCTV will sort out the big and small things that happened around us within 24 hours for you.
[concern]
A lot of information! These hot issues were answered by the press conference of the National People’s Congress

On March 4th, the second session of the 13th National People’s Congress held a press conference, and Zhang Yesui, a spokesman, answered questions from Chinese and foreign journalists.
● How to deal with the increasingly tough US policy toward China?
It should be noted that the interests of China and the United States have been deeply intertwined. I think a conflict and confrontation between China and the United States is not in the interests of either side. In addition, there is definitely no way out to deal with new problems under the background of globalization with the old thinking of the Cold War.
I think the essence of Sino-US economic and trade relations is mutual benefit and win-win, so we hope that both sides will continue to step up consultations and reach a mutually beneficial and win-win agreement.
● What are the considerations for formulating the foreign investment law?
The enactment of the foreign investment law is to innovate the legal system of foreign investment and replace the "three laws on foreign investment" (the law on Sino-foreign joint ventures, the law on foreign-funded enterprises and the law on Sino-foreign cooperative enterprises) and become the basic law for the utilization of foreign capital in China in the new era.
● The "Belt and Road" has caused some countries to fall into a "debt trap"?
The "Belt and Road" adheres to the principle of mutual cooperation, joint construction and sharing, and also adheres to the market-oriented operation mode.
Whether it is project selection or investment and financing cooperation, it is a decision made jointly by the participants.
China attaches great importance to the sustainability of debt, and will not impose on others in project cooperation, let alone create any traps.
● Will China’s rising defense expenditure threaten other countries?
China has always adhered to the path of peaceful development and implemented a defensive national defense policy. China’s limited defense expenditure is solely for safeguarding the sovereignty, security and territorial integrity of the country and will not pose a threat to other countries.
● Is the Personal Information Protection Law submitted for consideration this year?
The National People’s Congress Standing Committee (NPCSC) has included the enactment of a personal information protection law in this legislative plan, and relevant departments are studying and drafting it with a view to its early promulgation.
Important progress has been made in the case of Kang Mingkai, a Canadian national, suspected of committing a crime.
According to relevant departments, since 2017, Kang Mingkai has often entered the country with an ordinary passport and a business visa, stealing and spying on China’s sensitive information and intelligence through his contacts in China. Spavor Michael Peter Todd is an important intelligence relation of Kang Mingkai, who provides information to Kang Mingkai. Kang’s behavior is suspected of stealing and spying on state secrets and intelligence for overseas, which has seriously violated the laws of China. The relevant departments stressed that China is a country ruled by law, and will resolutely crack down on illegal and criminal activities that seriously endanger national security. At the same time, it will handle cases in strict accordance with the law and in a civilized manner, fully protect the legal rights of Kang Mingkai and Michael, and arrange consular visits and other related matters according to law. The case-handling department will start the next judicial procedure in due course according to the handling of the case.
[domestic]
China plans to launch 8-10 Beidou navigation satellites this year

According to the China Satellite Navigation System Management Office, this year, Beidou satellite navigation system will continue to build high-density global networks, and it is planned to launch 8-10 Beidou navigation satellites, complete the launch of all MEO (Medium Earth Orbit) satellites, further improve the constellation layout of the global system, and comprehensively improve the service performance and user experience of the system.
National Medical Products Administration: Three drugs, such as Weitongning tablets, were converted into prescription drugs.
According to the website of National Medical Products Administration, National Medical Products Administration recently issued an announcement on converting three drugs, such as Weitongning tablets, into prescription drugs and revising the drug instructions. The announcement clearly stated that Weitongning tablets, Huazhishuan and Xiaoshuan Tongluo preparations (tablets, capsules and granules) should be transferred out of the over-the-counter drug list and managed according to prescription drugs, and the above drug instructions should be revised at the same time.
[international]
Putin signed an order to suspend the performance of Intermediate-Range Nuclear Forces Treaty
Russian President Vladimir Putin signed an order to suspend the performance of Intermediate-Range Nuclear Forces Treaty on the 4th, which took effect on the same day. According to the Kremlin website, in order to take emergency measures to deal with the violation of Intermediate-Range Nuclear Forces Treaty by the United States, Putin signed relevant orders.
South Korea and the United States launched the "alliance" exercise, the scale was reduced, and the schedule was halved.

South Korea and the United States launched the joint command post exercise codenamed "Alliance" on March 4th. Compared with the previous "key decision" exercise, the exercise schedule was halved and the scale was reduced. South Korea and the United States recently announced that the joint military exercises codenamed "Key Decision" and "Vulture" will be stopped from this year, and the "Alliance" joint command post exercise will replace the "Key Decision" exercise.
China, a skyscraper built horizontally, surprised foreigners!

According to Future.com, recently, some foreign media were surprised to find that the world’s first horizontal skyscraper is about to be built in Chongqing, China. This covered bridge-shaped building with a length of more than 300 meters connects four skyscrapers at an altitude of 60 stories, instantly turning the building complex into a 3D "sail". The British "Daily Mail" used a full three-line headline to describe it like this: "China construction workers are about to build a huge commercial complex costing 2.7 billion pounds, and an incredible ‘ Horizontal skyscrapers ’ " .
Society
A college in Guangxi requires students to carry schoolbags in class? School: It is not mandatory.
Recently, an article entitled "A college in Guangxi requires students to carry schoolbags in class? School: I feel like playing around with a book in class. "The video became popular on the Internet. Some netizens questioned that this behavior is a mandatory requirement of the school and it is difficult to implement. In this regard, the school issued a statement saying that students are not forced to wear schoolbags, and they advocate the nature and voluntary principle from beginning to end.
The Forbidden City celebrates its 600th birthday: The Riverside Scene at Qingming Festival will be exhibited again.

Next year, the Forbidden City will celebrate its 600th birthday. The Palace Museum revealed on the 4th that it will launch dozens of high-quality exhibitions to show the charm of the 600-year-old Forbidden City. These exhibitions will be exhibited in the main hall of Wumen, the East-West Swallow Wing Building, the Wenhua Hall, the Wuying Hall, the East-West Six Palaces, the Shenwumen and other places, among which the highly sought-after "The Night Banquet of Han Xizai" and "The Riverside Scene at Qingming Festival" will meet the audience again in 2020.
[Sports]
The Spanish Embassy in China congratulated Wu Lei on his first goal: inspiring! Cheer for you
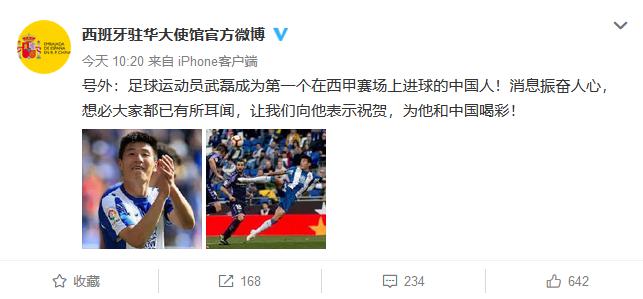
Last Saturday night, Lei Wu scored a goal to help Spain win Balado Lide. On the morning of March 4, Weibo, the official of the Spanish Embassy in China, also sent a congratulatory message to celebrate Lei Wu’s first goal in La Liga — — "Extra: Football player Wu Leicheng became the first China player to score in La Liga! The news is inspiring, and everyone must have heard about it. Let’s congratulate him and cheer for him and China! "
Li Junlin broke the national indoor record of men’s 800m.

The fourth race of the 2019 National Indoor Track and Field Championships was held in Xi ‘an, Shaanxi. The biggest surprise of the day came from the men’s 800-meter preliminaries. Li Junlin, the champion of the event in the 2018 National Athletics Championships, set a new indoor national record with a time of 1 minute 49.62 seconds.
[Entertainment]
Director Zheng Xiaolong talks about actors’ tax evasion: paying taxes according to law should start with children.

On the 4th, Zheng Xiaolong said that the reasons for tax evasion in the entertainment industry are: ① Some people are unwilling to pay taxes; (2) There is overlap or inconsistency between national tax policies and local tax policies; There is no education that should be taxed according to law in our education since childhood. He suggested that children should be given ideological understanding early, so that when they have more income, they will have the concept of paying taxes according to law.
[face]
[Yang Jie] Chairman of China Telecom was transferred to Chairman of China Mobile.

On March 4th, Yang Jie, the chairman of China Telecom Group Co., Ltd., was officially transferred to China Mobile as the chairman. On the morning of the 4th, China Telecom held a farewell ceremony to see Yang Jie off to take office in the China Mobile Office Building next door. Shang Bing, the 64-year-old former chairman of China Mobile, will retire at the age of.
[Luo Yazhou, Ying Xianyue, Wang Tongxiao] The three old people who kicked the door to put out the fire and save people received a bonus of 10,000 yuan: donated

On March 2, two octogenarians in Depingba Community of Quzhou caught fire in bottled liquefied gas. They panicked, climbed out of the window and shouted for help on the canopy on the second floor. Hearing the call for help, neighbors Luo Yazhou, 75, Ying Xianyue, 88, and Wang Tongxiao, 74, went retrograde at the first time, kicked the door into the room and put out the fire to save people. Even firefighters praised them for their "wisdom and courage and proper command".
According to a report in qianjiang evening news on March 5th, a platform plans to give 10,000 yuan to reward the old people. When the old people learned of the bonus, the result of negotiation was to donate the bonus to the community to transform the infrastructure. If there is any surplus, it will be donated to Master Sun’s house that caught fire.
[Ling Lao and Zhang Lao] Two "comfort women" survivors were found in Hunan.

Recently, in Yueyang, Hunan Province, 89-year-old Ling Lao and 91-year-old Zhang Lao bravely stood up, uncovered their scars and told their unfortunate experiences of being forcibly taken as "comfort women" by the Japanese army when they were girls. Up to now, there are only 15 survivors of "comfort women" registered in Chinese mainland.
[Words] 4-year-old boy speaks English so fluently. Netizen: I am not as good as a baby.

Recently, the video of a 4-year-old boy teaching English by words and deeds became popular on the Internet. In the video, it is surprising to speak pure English, and many netizens praise "English is better than me". Yan Yan’s mother said that Yan Yan can spell 2000 words now, and there is no need to learn English by rote. If English is integrated into life, children will naturally remember it.
See you at 8 o’clock tomorrow!
Editor: Xiao Xiao Cai Chunlin